What is Symbiotic?
Symbiotic is a shared security protocol designed to create a marketplace for economic security. It enables networks that need security to access it from those who have assets to stake, creating an efficient ecosystem where stake can be shared and utilized across multiple networks. Through its flexible architecture, stake providers can maximize their returns while networks can obtain the security guarantees they need.
Key Components and Relations
Core Participants
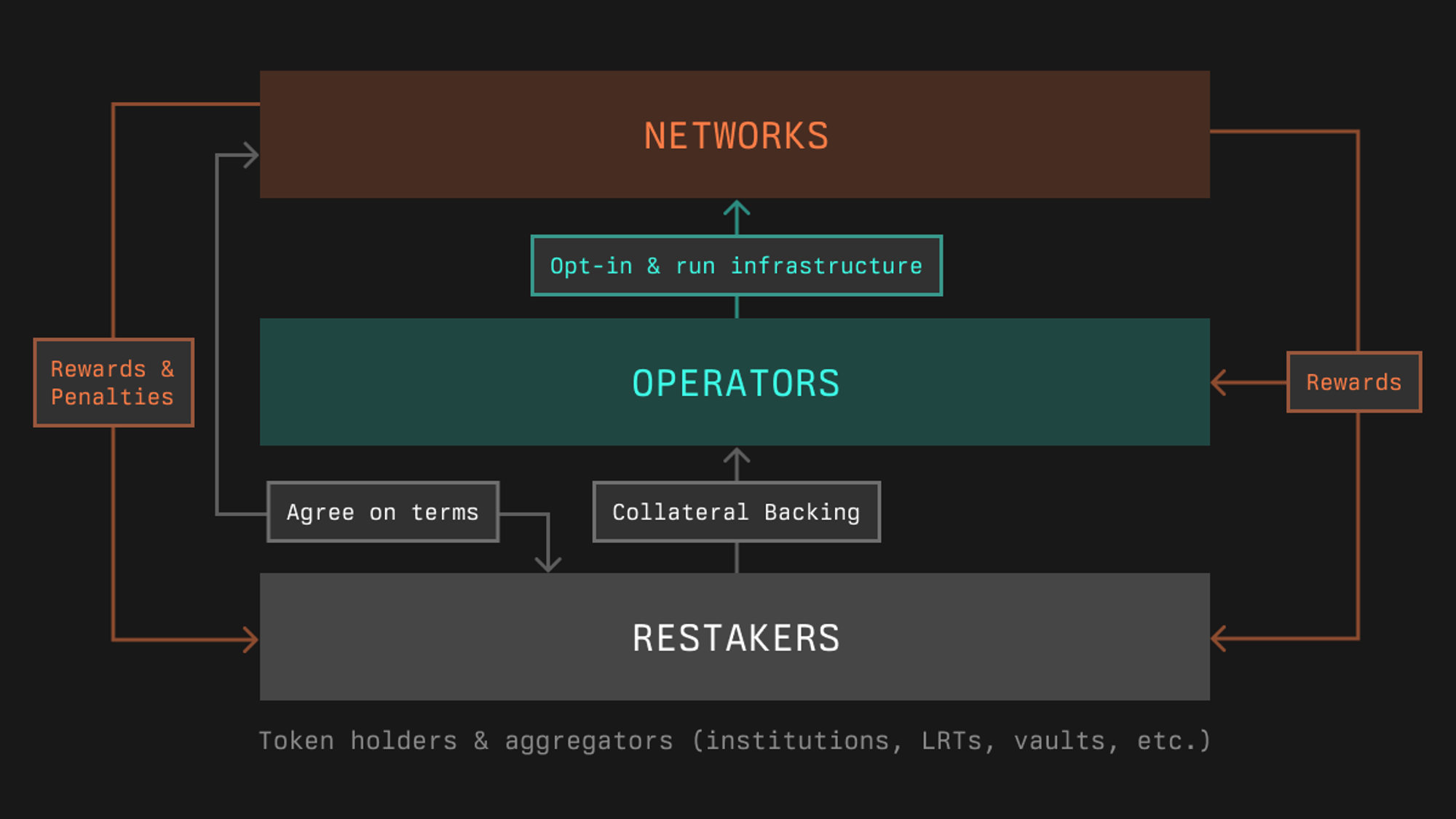
- Stakers - Entities looking to earn rewards by providing their assets as a stake through vault deposits. They can be individual token holders, institutions, or liquid (re)staking protocols. Stakers deposit funds into specialized smart contracts (vaults) managed by curators who handle delegation decisions.
- Networks - Systems that need economic security to operate safely. These can be Layer 1 blockchains, Layer 2 solutions, or other decentralized systems that require stake-based security guarantees.
- Operators - Professional entities that maintain network infrastructure by running validators, nodes, or other required systems. They receive stake allocations to perform their duties and are responsible for network operations.
Participant Connections
The three core participants - Stakers, Networks, and Operators - are connected through a sophisticated infrastructure layer. At the heart of these connections are Vaults, which serve as the primary interface between all participants.
Symbiotic coordinates and manages interactions in this ecosystem by:
- Enabling Stakers to deposit their assets into Vaults, where Curators manage delegation strategies and approve qualified Operators
- Facilitating Networks' access to security by connecting them with Vaults and their associated stake
- Allowing Operators to receive stake allocations through Curator-managed Vaults to perform their network duties
This interconnected system is monitored by Resolvers, who validate activities and ensure security across all connections. In the following sections, we'll explore the key infrastructure components, including Vaults, Curators, and Resolvers, in more detail.
System Relations
The Symbiotic protocol facilitates several critical interactions between participants, creating a robust and efficient security marketplace. Here's how these key components work together:
Stake Accounting
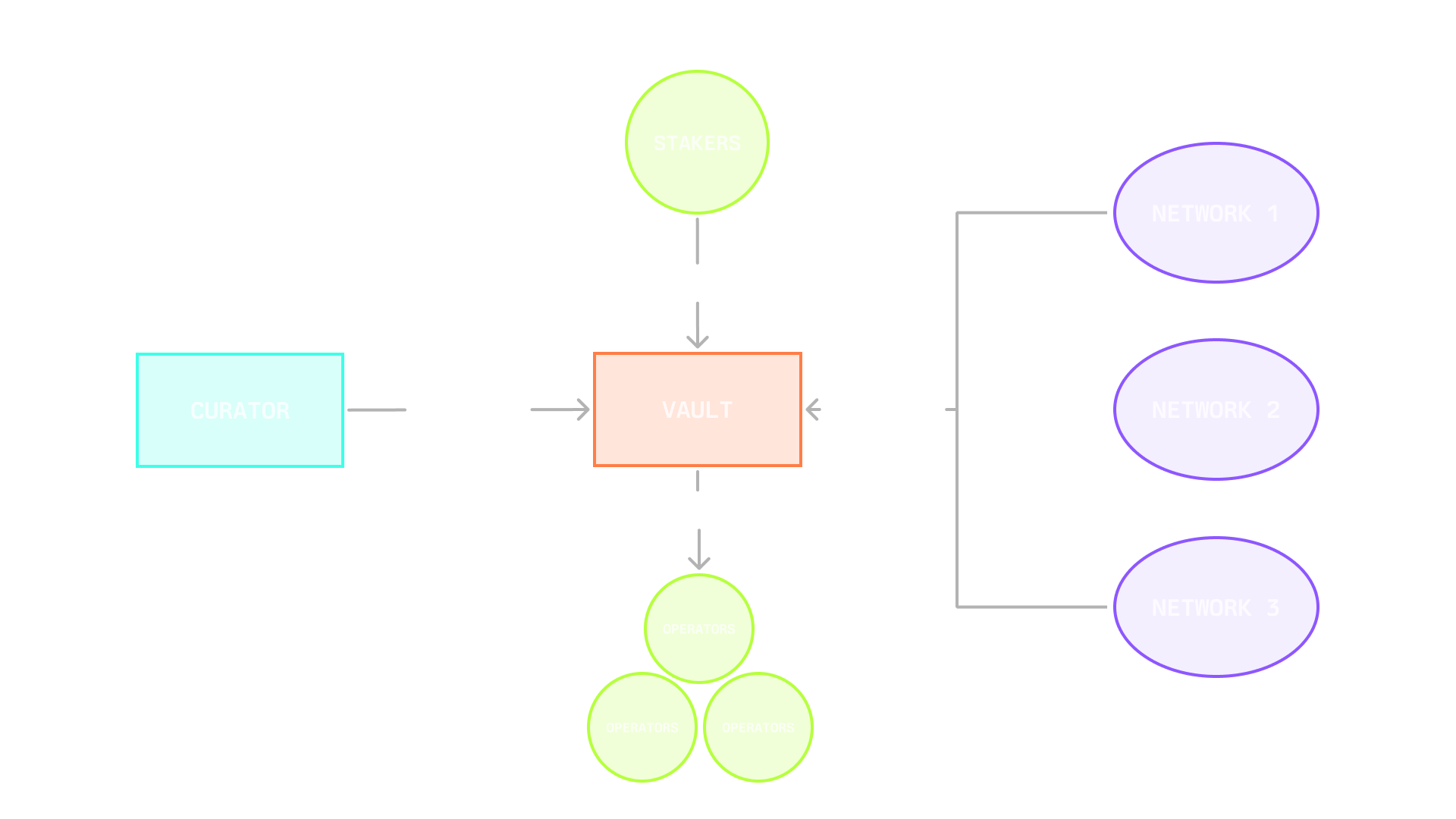
- Stakers deposit their assets into vaults
- Each vault is managed by a curator who controls stake allocation
- Curators delegate stake to qualified operators who run network infrastructure
- A single vault can serve multiple networks simultaneously, allowing efficient stake distribution across different operators
The stake delegation system has important characteristics:
- Assets remain securely locked in the vaults without actual transfer
- Stake delegation works through an accounting system only
- Assets can only leave the vault through:
- Original staker withdrawals
- Validated slashing events from networks
Network Operations
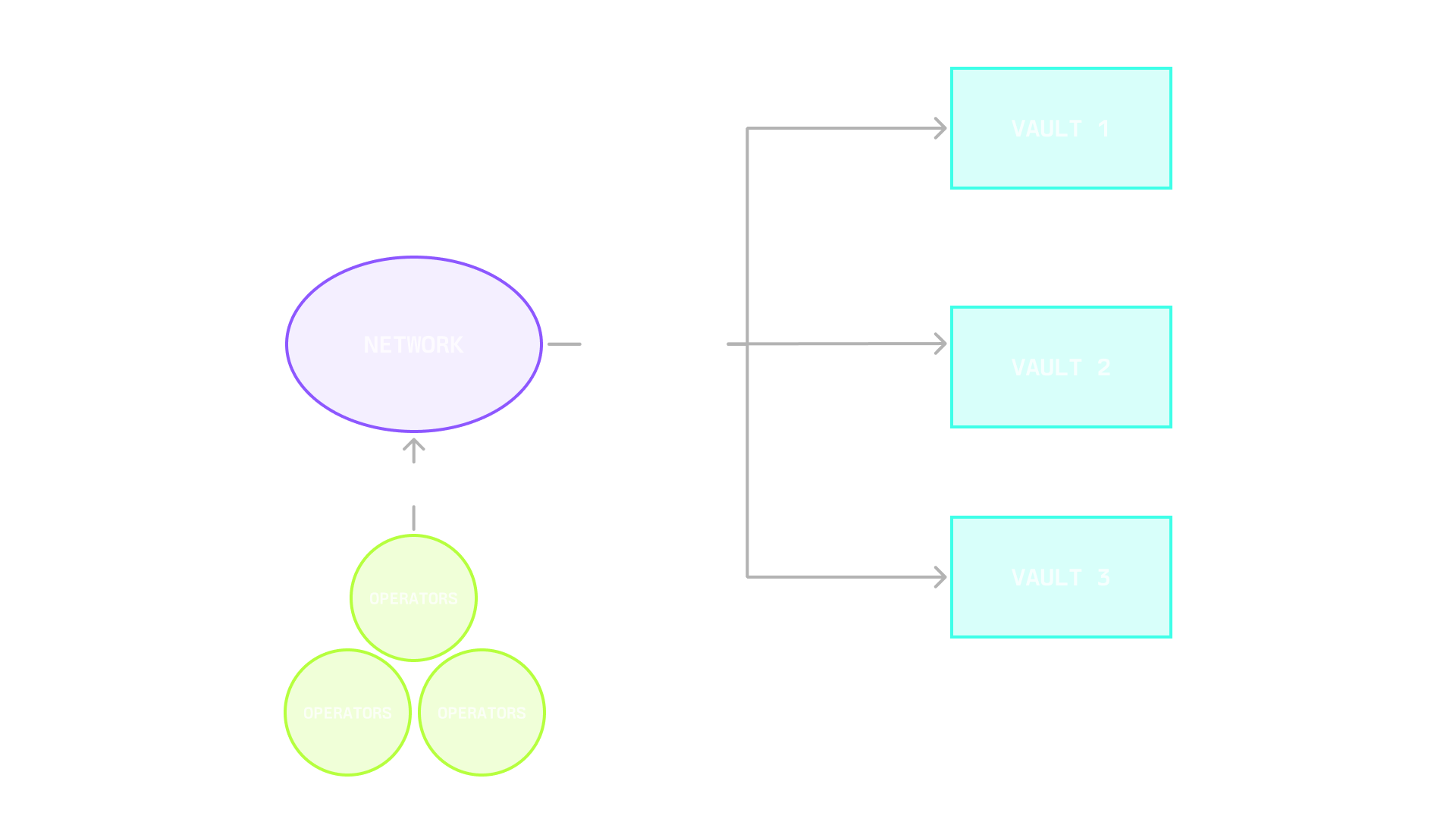
Networks work with multiple vaults simultaneously, allowing them to aggregate security from different sources. This flexible architecture enables operators to accumulate a stake across different vaults, while networks can calculate their total stake by combining delegation from various vault sources.
Slashing process
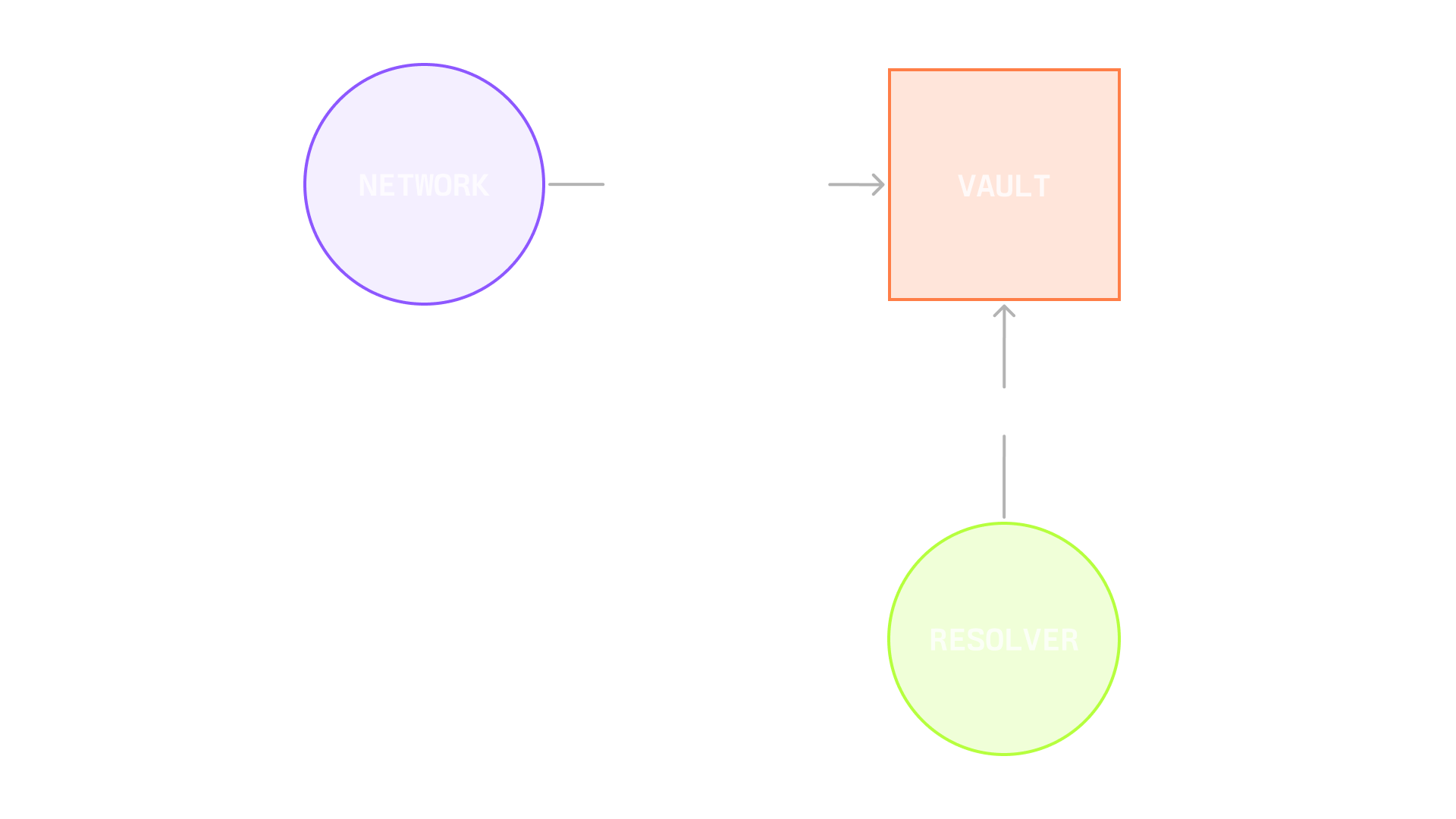
- Networks can initiate the slashing of operators by interacting with vaults where operators have a stake
- Networks can choose which vaults to slash from if an operator has a stake in multiple vaults
- Resolvers act as validators of slashing events with veto power
Resolvers can be automated contracts, slashing committees, dispute resolution frameworks, multisig wallets, or DAO governance systems. Networks and vault curators agree on which resolvers to use (or not to use any resolver at all) and slashing terms. During slashing, networks choose vaults to slash from, resolvers review the event and can veto invalid slashing attempts.
Benefits of the Architecture
- Capital Efficiency: Assets can be utilized across multiple networks simultaneously
- Flexibility: Networks can customize their security model through different vault compositions
- Risk Management: Stake can be isolated or shared based on specific security requirements
- Scalability: The modular design allows for easy integration of new networks and operators
This architecture creates a sustainable ecosystem where security providers (stakers and operators) and security consumers (networks) can interact efficiently while maintaining their specific requirements and risk preferences.