Operators
Description
Operators are entities running infrastructure for decentralized networks within and outside of the Symbiotic ecosystem. The Symbiotic protocol creates a registry of operators, logs interactions with the protocol, and protocol participants can attach credentials and other data to operator entities. In the initial version, this encompasses operator entity metadata provided by the operators themselves, as well as data created by interacting with the Symbiotic protocol, such as:
- Networks that the operator opted into
- Associated vaults and restaked collateral from vaults
- Historical logs of slashings and all other interactions with the Symbiotic ecosystem
An important benefit of the Symbiotic protocol and its enshrined vault system is the ability for operators to receive a stake from different partners (through vaults) to the same set of node infrastructure per supported network. This system allows node operators to acquire the stake from a diverse set of stakers with differing risk profiles without needing to set up isolated infrastructure for them.
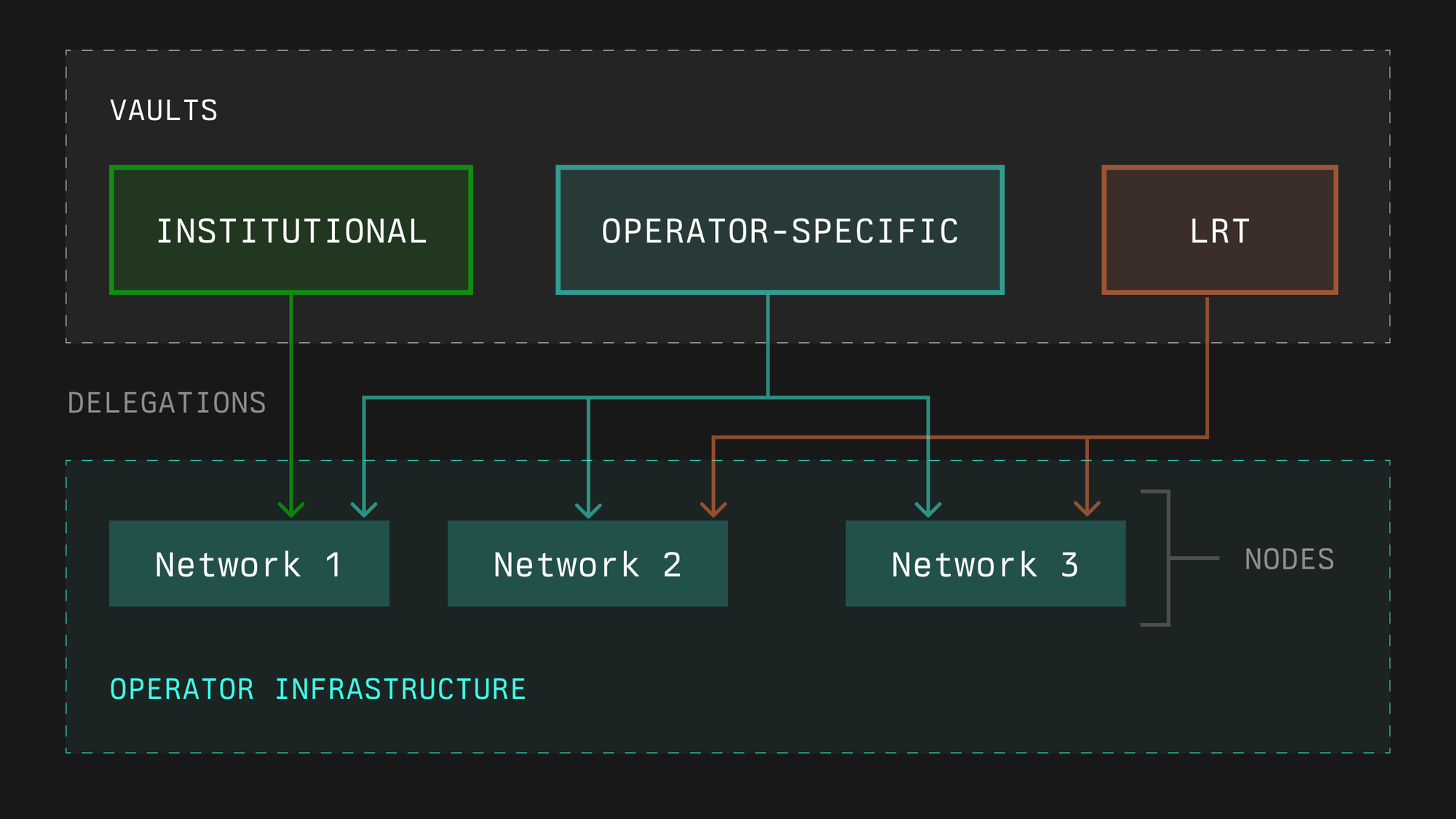
In the future, we envision the Symbiotic protocol to contain a rich set of verifiable data and curated credentials about node operators. This will enable future networks using Symbiotic to source security for their use case to utilize innovative and maximally capital-efficient reputation-based operator selection mechanisms.
Technical overview
In Symbiotic, the operator can be either an EOA or a contract registered in the OperatorRegistry.
Vaults
Let the Vault be , the Delegator module of the vault is and the Slasher module is .
To raise the stake, the operator must opt into networks and vaults by calling the optIn() method in the NetworkOptInService and VaultOptInService accordingly. The OPERATOR_NETWORK_SHARES_SET_ROLE/OPERATOR_NETWORK_LIMIT_SET_ROLE holder then allocates the stake to the operator by calling D.setOperatorNetworkShares()/D.setOperatorNetworkLimit() (depends on the delegator’s type).
Networks
The operator opts into the network to validate it. Based on various factors, such as reputation, stake amount, and other relevant criteria each network independently decides whether to include the operator in the active operator set or not.
Slashing
The operator’s stake becomes active and subject to slashing immediately after the opt-in process to both the network and the vault. However, the corresponding role in the vault can apply the timelock for allocating a stake for additional guarantees for operators. The slashing process is implemented in (the vault’s Slasher module).